-
Contact Us

- TOP
NPCore's core technologies for APT defense include behavior-based detection, dual-layer defense systems, and real-time threat response capabilities.
Network APT
Home
Products & Services
Network APT
NPCore's APT defense utilizes AI-based behavior detection technology and a dual-layer defense system to protect networks and endpoints, enabling real-time responses to advanced APT threats such as ransomware and new or evolving malware.
ZombieZERO Inspector N
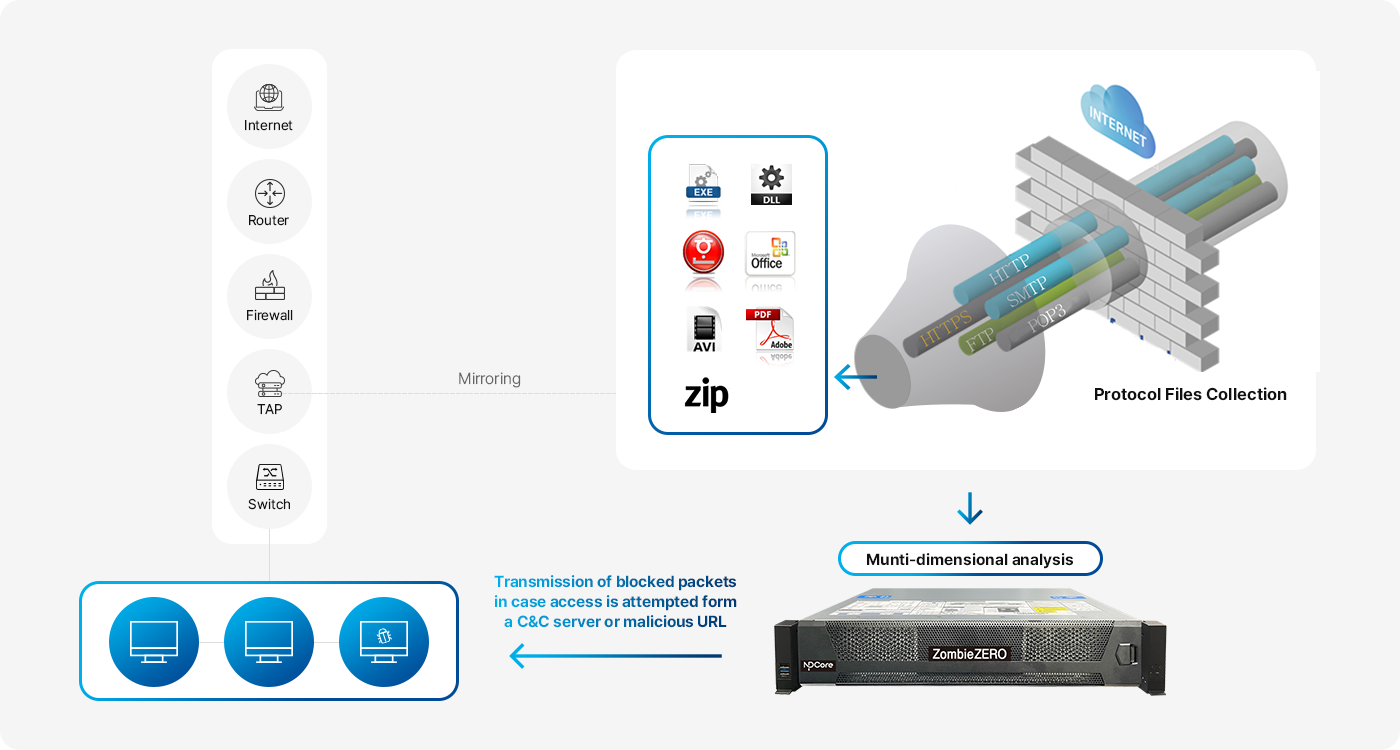
APT solution that detects and blocks malware coming through network traffic-

GS Certification
The ZombieZERO Inspector N is a security solution that detects, analyzes,
and blocks new and variant malware by collecting valid data from network traffic.
It responds to and defends against network APT (Advanced Persistent Threat) attacks using
virtual analysis machines to analyze information such as URLs/Files collected from the network.
It utilizes behavior-based multi-dimensional analysis (anti-virus engine, static YARA,
dynamic behavior analysis, reputation analysis) to detect unknown new and variant malware,
enabling proactive response to potential internal threats.

NPCore's APT defense prevents data loss and downtime from advanced APT threats, ensuring business continuity. This defense system improves visibility across networks and endpoints, providing a sustainable solution for evolving threats.

-

Malware and Abnormal Traffic Detection/Analysis
-

Malware Response and Treatment
-

Integrated Monitoring and Management
- Bidirectional network traffic monitoring for file ingress and egress
- Collection and analysis of major internet service protocols (HTTP, HTTPS, SMTP, POP, IMAP, etc.)
- Multi-dimensional malware analysis: Pattern-based (blacklist/whitelist), antivirus, YARA rule-based static analysis, behavior-based sandbox dynamic analysis, reputation analysis, etc.
- Engine dedicated to non-executable (non-PE) malware – JS/SWF, documents (Hangul, MS Office, PDF, Flash, Image, Media, etc.)
- Detection and blocking of access to harmful sites and C&C communication
- Security status monitoring through dashboard and providing information on key events (malware ingress and abnormal traffic)
- Detailed behavior analysis log information for files/processes/registry/network, etc.
- Provision of analysis reports, notification of key security events (E-mail, SMS, etc.)
- Flexible security scalability (integration with similar APT response products, email APT, file APT response products, EDR solutions, reputation analysis - API integration with VirusTotal, etc.)
- Log/configuration file backup function (automatic/manual)
- Syslog forwarding for integration with security management (SIEM, ESM) solutions
- Detection, blocking, and isolation of malware distribution sites and C&C communication
- Redirection to a landing page by sending blocking packets upon access to malicious URL/IP
- Provision of PCAP (Packet Capture) file for network access history of malicious files
-
 Threat Detection/Analysis
Threat Detection/AnalysisReal-time extraction of downloaded file/URL information from network traffic
Behavior-based analysis to complement Zero-day vulnerabilities undetected by conventional signature-based security systems
-
 SSL Traffic Analysis
SSL Traffic AnalysisFunction to analyze and block encrypted traffic (HTTPS) in conjunction with SSL decryption devices
-
 Global Pattern Update
Global Pattern UpdateDomestic live updates provided: integration with KISA C-TAS, ECSC (Cyber Safety Center)
Global live updates provided: antivirus (Bitdefender), VirusSign, VirusTotal
-
 International Certification
International CertificationInternational CC (EAL2) Certification
GS Certification
-
 User Expandability
User ExpandabilitySecurity scalability provided by applying multi-dimensional analysis engines
Correlation analysis function through integration between APT products
Customization for user analysis environment and establishing a similar analysis environment
Integration with third-party antivirus engines and reputation services
-
 Malware Expert Analysis Team
Malware Expert Analysis TeamProviding more refined analysis results through correlation analysis using equipment-specific data, AI machine learning (supervised/unsupervised learning)
Immediate response and manual analysis reports provided by a dedicated malware analysis team
NPCore's APT defense overcomes the limitations of traditional signature-based detection technologies by adopting AI-powered behavior-based detection. This advanced defense system analyzes attack patterns and behaviors to identify and block even unknown APT threats in real time. Additionally, it establishes a dual-layer APT defense strategy that protects both networks and endpoints simultaneously, enabling comprehensive handling of threats from multiple vectors. By responding to sophisticated APT attacks such as ransomware and advanced malware in real time, NPCore's defense solutions effectively safeguard corporate data and systems.
Blocking access to C&C servers and malicious URLs through blocking packets
-
01
Improved Detection and Response Capability for Intelligent Threats (APT)
Provides special technology and algorithms to detect and respond to Advanced Persistent Threats (APT).
This helps identify threats that were difficult to detect with traditional security systems.Multi-dimensional detection/analysis process
Behavior detection, analysis, and blocking using virtual machines (sandboxes)
Application of virtual machine bypass prevention technology: Inducing the behavior of malware that bypasses virtual machines for dynamic behavior detection and analysis
-
02
Rapid Response
Provides visibility and automated response features for detected threats, shortening incident response time and enabling quick responses to security incidents.Use of collection-dedicated acceleration boards for network traffic collection
MITRE ATT&CK classification
Providing malicious activity flowcharts
-
03
Response Utilizing Evidence-Based Threat Intelligence
Real-time updates and alerts on threats allow for threat information sharing among various organizations, enabling better security responses.Ministry of Education Cyber Safety Center ECSC
Official integration with Yara Rule
Domestic and global pattern live updates
-
04
Security Management and Forensic Analysis Support
Generates and stores records of security events and attack activities, supporting forensic analysis and incident investigation.Ability to understand the security level of the managed target, status of malicious file analysis, key events, and current situation information
Notation of attack tactics, techniques, and procedures through MITRE ATT&CK classification in conjunction with malicious activity flowcharts
| Model | Network APT Series | |||||
|---|---|---|---|---|---|---|
| 300N | 500N | 1000N | 2000N | 5000N | 10000N | |
| Chassis Type | 1U | 2U | 2U | 2U | 2U | 2U |
| Traffic Coverage | ~ 300Mb | ~ 500Mb | ~ 1Gb | ~ 10Gb | ~ 20Gb | ~ 40Gb |
| CPU |
Bronze 3204 1.9GHz (6Core)*2 |
Silver 4310 2.1GHz (12Core) |
Silver 4310 2.1GHz (12Core)*2 |
Gold 6326 2.9GHz (16Core)*2 |
Gold 6330 2.0GHz (28Core)*2 |
Gold 6348 2.6GHz (28Core)*2 |
| Memory | 48GB | 64GB | 96GB | 160GB | 320GB | 640GB |
| SSD | 960GB(Raid1) | 960GB(Raid1) | 960GB(Raid1) | 960GB(Raid1) | 960GB(Raid1) | 960GB(Raid1) |
| Storage | 960GB | 960GB | 960GB | 1.92TB | 1.92TB*2 | 1.92TB*6 |
| Network Interface (Basic) | 1GbE 2port | 1GbE 2port | 1GbE 2port | 1GbE 2port | 1GbE 2port | 1GbE 2port |
| Network Interface (Option) | 1/10G SFP+ 4port (Optical) | 1/10G SFP+ 4port (Optical) | 1/10G SFP+ 4port (Optical) | 1/10G SFP+ 4port (Optical) | 1/10G SFP+ 4port (Optical) | 1/10G SFP+ 4port (Optical) |
| Traffic Collection Interface | 4 X 1GbE Cooper | 4 X 1GbE Cooper | 4 X 1GbE Cooper | 4 X 10GbE SFP | 4 X 10GbE SFP | 4 X 10GbE SFP |
| Power Supply | Redundant 1300W | Redundant 1300W | Redundant 1300W | Redundant 1300W | Redundant 1300W | Redundant 1300W |

